Optimization

Arbor Networks Sightline (Arbor SP\TMS)
- Written by: Владимир
Identify Potential Network Outages & Gain Business Insights to Solve Your Problems
The network is the business. Operators must optimize resources, reduce service availability threats and thus save money. Arbor Sightline provides robust capabilities from network-wide capacity planning, to identifying and managing the mitigation of threats to the network.
This pervasive network data can also be leveraged to make routing and peering design decisions, lower transit costs, eliminate network threats and provide your business with new revenue-generating services.
Features:
- Network Peering Analysis. Your network delivers value to customers and users when it connects to other networks. Peering analysis helps determine what traffic can transfer off expensive transit links to either free peering or even become revenue-generating as a new customer.
- Network Capacity Management. You can employ Arbor Sightline to monitor the capacity of network infrastructure, which allows you to avoid saturation and re-engineer network traffic for more efficient utilization.
- Network Capacity Management. You can employ Arbor Sightline to monitor the capacity of network infrastructure, which allows you to avoid saturation and re-engineer network traffic for more efficient utilization.
Other products

Arbor Insight
- Written by: Владимир
Intelligent Visibility into Network Traffic
By providing intelligent visibility into network traffic and attaining insight into where traffic is coming from, Sightline with Insight enables more accurate traffic engineering, network planning and peering analysis – all of which helps reduce costs and optimize services.
Arbor Insight is designed to enhance the capabilities and workflows of Arbor Sightline. Together, they enable network operators to gain even more pervasive network flow monitoring while conducting agile, multi-dimensional, visual analysis against a combination of binned and annotated raw flows.
Other Products

Netscout NPM nGeniusONE
- Written by: Владимир
The nGeniusONE® solution provides real-time visibility into any infrastructure environment – data center, private & public cloud, remote offices, and co-locations. Leveraging NETSCOUT® Smart Data, nGeniusONE delivers smarter analytics for all their applications including voice, video, data, SaaS, UCaaS, and even custom applications from wherever they are accessed – headquarters, regional locations, or home offices.
nGeniusONE is the foundation of NETSCOUT’s nGenius Enterprise Performance Management solution, providing continuous network and application monitoring and end-user experience assurance to support today’s modern enterprises. The solution's insights increase the IT-team's understanding of consumption patterns, application utilization, and overall digital experience to better support resource optimization and capacity planning.
Features:
- Performance Analysis. At-a-glance views into overall network and application performance to help keep your business up and running enterprise wide.
- Service Dependency Mapping. Reduces migration risk by visualizing “hidden” client/server relationships and application service dependencies.
- Session and Application Analysis. In-depth, application performance analysis including business and protocol-specific monitors, with metrics for troubleshooting and improving performance and end-user experience.
- Synthetic Testing. Views into the results of configurable business transaction tests to detect changes in performance trends for early warning of degradation in digital user experience quality.
Other Products

Enterprise
- Written by: Владимир
Complete your journey to zero-touch, application-based security policy automation. Integrate network and cloud security processes, achieve zero-touch change automation, and consolidate on-premise and multi-cloud policy management under a single control plane.
"The value becomes apparent when a workload that took 40 people, now takes about 5 people."
– Large U.S. Utilities Company, Senior Cybersecurity IT Solutions Engineer
Consolidate complexity under a single control plane.
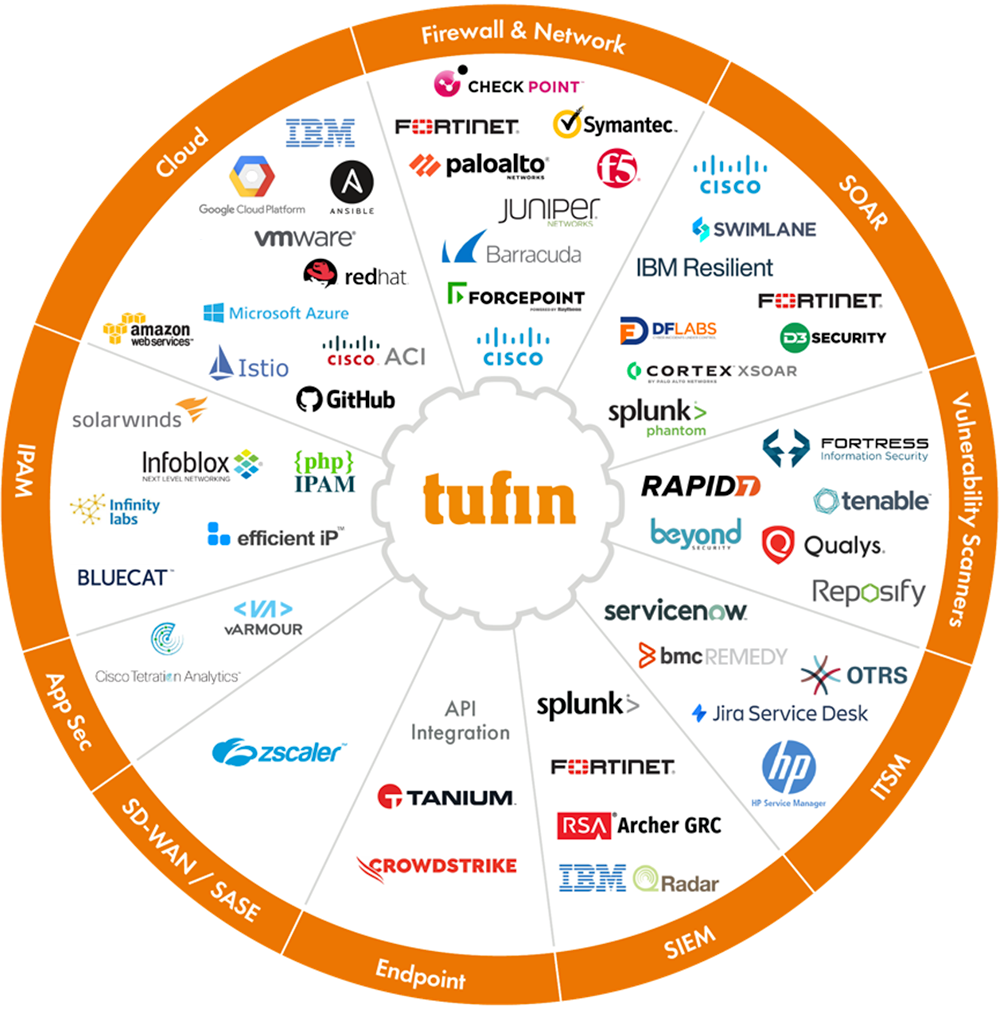
One reason 2,900+ organizations have trusted Tufin for network security policy management (NSPM) is that we have the broadest integration ecosystem in the NSPM space, including AWS, Azure, Check Point, Cisco, Forcepoint, Fortinet, Juniper, and Palo Alto Networks. Tufin will make it easier for you to gain network security maturity and achieve end-to-end automation and provisioning across your heterogeneous environment.
Integrating Tufin with these solutions is also easier via our code-free, GUI-based integration options. We make it easier for you to gain network security maturity and achieve end-to-end automation and provisioning across your heterogeneous environment.
Achieve zero-touch automation from access request to provisioning.
Tufin can automate even the most complex change management processes to virtually eliminate manual tasks, minimize human error and reduce cyber risk. You can build end-to-end workflows, where if the Tufin-recommended changes are approved by the administrator, Tufin will automatically implement the changes.

Extend network security policy orchestration and automation to the cloud.
Only Tufin provides agentless, multi-cloud policy management. Take full advantage of cloud-native infrastructure, maintain enterprise-wide visibility and control, and optimize segmentation across on-premise and cloud.
Integrate security guardrails into the CI/CD process.
Tufin easily integrates into your CI/CD process to serve as the security gatekeeper for your DevOps team, so they don’t need to change how they work. Tufin will alert on access changes that violate segmentation policies and proactively block the changes pre-deployment. This simple step can vastly reduce risk for your organization while trimming workload.

Deploy applications fast with connectivity management.
Break down silos between teams by providing a central console for all network-related application changes, ensuring that the network is always aligned with changing application requirements.
Tufin makes it easy to define, implement, monitor, maintain and decommission application connectivity through a highly automated process. It also provides graphical diagnostic tools that help you troubleshoot and automatically repair connectivity issues.

Tufin easily scales to support massive, complex enterprise networks.
Designed for scalability, more than 2,900 organizations, ranging from small offices to large enterprises and MSSPs, have trusted Tufin as their network security policy management solution.
More than half of the Fortune 50, 19 out of the 20 largest multinational, consumer banks and many other large and complex enterprises rely on Tufin to simplify network security management.
- The most comprehensive network topology mapping with support for 100M+ routes
- Virtually unlimited scale with distributed architecture
- High availability with highly redundant, multi-node clusters
- The broadest ecosystem integration available

Tufin Orchestration Suit: A Unique Solution for the Ukrainian IT Market in NWU's Portfolio
Tufin Orchestration Suit is a truly advanced and unique solution from a global leader in cybersecurity, now available in the Ukrainian IT market through NWU, Tufin's official distributor in Ukraine. This gives you the opportunity to purchase Tufin in Ukraine. Tufin Orchestration Suit is a coveted solution for SOC teams in any Ukrainian company.
To purchase Tufin or for more information and consultation on the new features of Tufin TOS R24-1, please contact
Other Products

SecureTrack+
- Written by: Владимир
Centralize network security policy management, risk mitigation and compliance monitoring across firewalls, NGFWs, routers, switches, SDN and hybrid cloud.
"We save countless hours on rule cleanup and compliance reporting, and we can give management visibility without pulling one of our valuable team members from critical tasks." - Cybersecurity Manager, Large U.S. Utilities Company
Centralize network security policy management and simplify segmentation.
Gain holistic visibility, and consolidate the management of your network segmentation policies across on-premises and cloud. SecureTrack+ allows you to establish a baseline of allowed and blocked traffic between security zones and monitor in real time for violations, making it easier to implement and manage consistent network segmentation
Security Policy Builder
Then Tufin monitors network traffic logs in real time to illuminate the gaps between your desired segmentation and reality, providing instruction on the changes required to close those gaps.
IPAM Integration
SecureTrack+ automatically populates and maintains any subnet changes, increasing the accuracy of risk assessments and violation alerts.
Automated firewall rule and network object cleanup delivers immediate ROI.
Firewall Rule Cleanup
SecureTrack+ automatically detects and alerts on unused, shadowed, redundant, overly permissive rules and enables automatic rule decommissioning. Tufin clients have reduced their time spent on rule cleanup by 90%.
Automatic Unused Object Identification and Network Object Decommissioning
SecureTrack+ can identify and remove network objects (server/subnet/range), which are no longer used due to hardware replacement or network architecture changes.

Consolidate and automate firewall management and rule base optimization.
Tufin provides a central repository of all the firewall rules and objects to simplify firewall management across multi-vendor, multi-platform technologies. An advanced search and filtering mechanism reduces the time and effort associated with firewall management.
The Automated Policy Generator automatically determines, based on existing traffic, who/what truly requires access, optimizing firewall rule bases in accordance with least privilege principles. This unique capability not only makes firewall optimization attainable for overstretched firewall teams, but it allows optimization to become part of a repeatable firewall management process.

Compliance monitoring across thousands of network and cloud resources provides real-time risk awareness.
Network and security teams can see risky access and firewall security policy violations in real-time from a central dashboard and receive alerts. SecureTrack monitors network changes and compares them to security/compliance policies, prioritizing violations by criticality.
Vulnerability Mitigation
SecureTrack+ integrates with your vulnerability management solution, allowing you to correlate network intelligence with vulnerability scanning data. This allows you to prioritize patching faster.

Extend network security policy orchestration and automation to the cloud.
Only Tufin provides agentless, multi-cloud policy management. Take full advantage of cloud-native infrastructure, maintain enterprise-wide visibility and control, and optimize segmentation across on-prem and cloud.
Integrate security guardrails into the CI/CD process.
Tufin easily integrates into your CI/CD process to serve as the security gatekeeper for your DevOps team, so they don’t need to change how they work. Tufin will alert on access changes that violate segmentation policies and proactively block the changes pre-deployment. This simple step can vastly reduce risk for your organization while trimming workload.

Make data center migration and hardware expansion faster and safer.
The network object policy cloning workflow dramatically reduces manual tasks and the human error associated with data center migration, hardware expansion and/or hardware replacement, as it automatically clones the security policy of existing servers/subnets/ranges to newly added ones.

Reduce audit prep by up to 90%.

In addition to real-time compliance monitoring for risky changes and violations, SecureTrack+ provides an automated audit trail that allows you to rapidly generate a variety of customizable audit reports that comply with regulatory standards, such as PCI-DSS, SOX, NERC-CIP, HIPAA, GDPR and more. This is your first step towards continuous compliance.
Tufin Orchestration Suit: A Unique Solution for the Ukrainian IT Market in NWU's Portfolio
Tufin Orchestration Suit is a truly advanced and unique solution from a global leader in cybersecurity, now available in the Ukrainian IT market through NWU, Tufin's official distributor in Ukraine. This gives you the opportunity to purchase Tufin in Ukraine. Tufin Orchestration Suit is a coveted solution for SOC teams in any Ukrainian company.
Purchase Tufin or for more information and consultation on the new features of Tufin TOS R24-1, please contact
Other Products

SecureChange+
- Written by: Владимир
Achieve continuous compliance and reduce network change SLAs by up to 90% with network change design automation and rule lifecycle management.
"ROI on our Tufin investment has been great. It was, and still is, driven by productivity gains, reduction of re-work from manual errors and automated coordination across teams"- Head of Firewall Management Team, Big 4 Professional Services Firm
Eliminate network change and rule review backlogs.
Tufin lets your team do more with existing resources by providing flexible workflows and automation that can dramatically reduce your time spent on network changes and rule lifecycle management.
Repeatable, auditable and policy-driven processes also reduce risk for your organization, while making it easier for you to implement and maintain more advanced network segmentation.
Tufin integrates with leading ITSM solutions, allowing for a ticket in your ITSM to trigger a workflow within Tufin.
Workflow Examples:
- Access/Decommission Request
- Group Modification
- Rule Modification
- Rule Recertification

Fully Automated with SecureChange+
Unlock end-to-end change automation, including automated change provisioning with Tufin Enterprise.
Automate rule lifecycle management.
Tufin orchestrates rule review across owners with an automated recertification process. It identifies expiring or expired rules and maps them to owners, eliminating many of the manual steps normally required.
- Customize your rule review process.
- Identify inactive owners for rule reassignment.
- Orchestrate rule review across owners.
- Automate rule certification, changes when needed, and decommissioning when appropriate.
- Maintain a consistent audit trail.

Reduce downtime with network topology intelligence that supports 100M+ routes.
SecureChange+ topology intelligence and dynamic mapping powers many of the capabilities that set Tufin apart from the competition.
- Highly accurate target selection and visualization of proposed change designs
- Verification that access was successfully added
- Path analysis enables investigation of traffic paths for fast troubleshooting
- Simulating and managing network traffic paths (e.g. managing multi-cloud paths)

Proactive risk assessment incorporates third-party security intelligence.
SecureChange enables continuous compliance with internal policies and industry regulations, such as PCI-DSS, NERC-CIP, and HIPAA.
Proactive risk assessment is part of the network change design process. This vets proposed changes against your security/compliance policies, and it can be customized to cross-reference intelligence from third-party solutions, such as vulnerability management tools, SIEM, SOAR and endpoint threat detection tools.
Extend network security policy orchestration and automation to the cloud.
Only Tufin provides agentless, multi-cloud policy management. Take full advantage of cloud-native infrastructure, maintain enterprise-wide visibility and control, and optimize segmentation across on-prem and cloud.
Integrate security guardrails into the CI/CD process.
Tufin easily integrates into your CI/CD process to serve as the security gatekeeper for your DevOps team, so they don’t need to change how they work. Tufin will alert on access changes that violate segmentation policies and proactively block the changes pre-deployment. This simple step can vastly reduce risk for your organization while trimming workload.

Inject vulnerability awareness into the change design process.
Vulnerability-based Change Automation (VCA) integrates vulnerability awareness into the change design process, by checking for vulnerabilities on source and destination during the change design process.

Gain advanced audit readiness with enterprise-wide change logging.
As with SecureTrack+, SecureChange+ provides real-time compliance monitoring and a variety of customizable audit reports that align with regulatory standards, such as PCI-DSS, NERC-CIP, HIPAA, GDPR and more. However, SecureChange+ enables a more advanced state of audit readiness by providing a comprehensive audit trail for network changes, including full change accountability and audit-ready reports. All related tickets and every change is logged and reportable.

Tufin Orchestration Suit: A Unique Solution for the Ukrainian IT Market in NWU's Portfolio
Tufin Orchestration Suit is a truly advanced and unique solution from a global leader in cybersecurity, now available in the Ukrainian IT market through NWU, Tufin's official distributor in Ukraine. This gives you the opportunity to purchase Tufin in Ukraine. Tufin Orchestration Suit is a coveted solution for SOC teams in any Ukrainian company.
Purchase Tufin or for more information and consultation on the new features of Tufin TOS R24-1, please contact
Other Products

NETSCOUT Omnis Security
- Written by: Владимир
Deep Packet Inspection-Based Network Visibility, Threat Detection, and Response.
Problems We Solve:
- Comprehensive Network Visibility. Packet-level visibility across your entire digital infrastructure is fundamental for effective cybersecurity.
- Real-time Threat Detection at Source. Scalable deep packet inspection and actionable, ML-based analytics at source of packet capture detect cyber threats in real time.
- Retrospective Threat Investigation and Hunting. Verify, detect or hunt for cyberthreats with rapid, retrospective investigation of laver 2-7 metadata and network packets.

Platform NETSCOUT Omnis
Advanced, Deep Packet Inspection-Based NDR.
Highly scalable, deep packet inspection-based comprehensive network visibility, ML-based real-time and historical cyber threat detection at source and integration into existing cybersecurity ecosystem for improved incident response and reduced risk.
Other Products

Packet Flow Switches (PFS) and TAPs
- Written by: Владимир
Deliver cost-effective and complete packet visibility while streamlining your monitoring architecture and reducing security risks.
Strategic Packet Visibility for the Connected World. NETSCOUT’s disaggregated packet flow switch architecture enables strategic packet visibility that scales and operates dynamically, enabling pervasive visibility with NETSCOUT's InfiniStream® appliances (part of the nGeniusONE® Service Assurance platform) or security systems, regardless of infrastructure modifications or changes in the source of network traffic. With TAPs and packet flow switches from NETSCOUT, service assurance, security assurance, and other monitoring tools can be physically anywhere and logically everywhere.

Features
The NETSCOUT nGenius® packet flow switch (PFS) and TAPs family enables multiple IT groups to aggregate, replicate, and manage the flows of traffic throughout the monitoring network, whether it’s for application performance monitoring, unified communications (UC), or security. Traffic management and security enablement capabilities ensure risk-free deployment of inline security and threat detection systems.
- Scalable Network Visibility. As your networks and traffic volumes grow, so too should your readiness to respond to issues as they arise.
- Active Inline Security. Inline packet flow switch deployments enable a pervasive defense architecture for inline and passive network protection.
- Decryption for Inline or Passive Tools. Inline or passive decryption gives visibility in the face of pervasive encryption.
- Eliminate Disruption to Traffic or Protocol Transactions. Simplify traffic acquisition and distribution for diverse network monitoring applications including performance management, service delivery management, and security monitoring.
Other Products

Vision One
- Written by: Владимир
Test network equipment
